Splunk Command's/Queries & Basic Structure/Components &More...
What is Splunk_?
machine-generated data gathered from the websites, applications,
sensors, devices etc..
• Why we use Splunk__?
• Splunk Architecture..
Splunk's architecture typically consists of the following components:
👇🏻
1. Forwarders : These are lightweight agents installed on data sources like servers, applications, or devices. They collect data and forward it to the Splunk indexer.
2. Indexers: Indexers receive data from forwarders, index it, and store it in searchable indexes. They handle search requests and provide data querying capabilities.
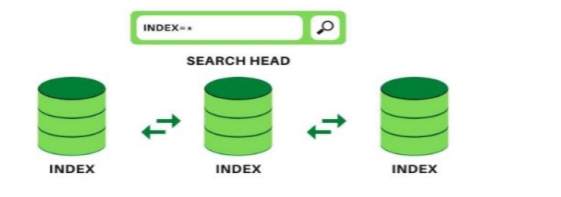
3. Search Heads : Search heads provide the user interface for interacting with Splunk. They accept search requests from users, send them to indexers for processing, and display the results.
4. Deployment Server : This component is used for managing configurations across multiple forwarders in a distributed environment.
5. Cluster Master : In a clustered environment, the cluster master coordinates activities among the indexers to ensure data replication and availability.
6. License Master : This component manages Splunk licenses across the deployment.
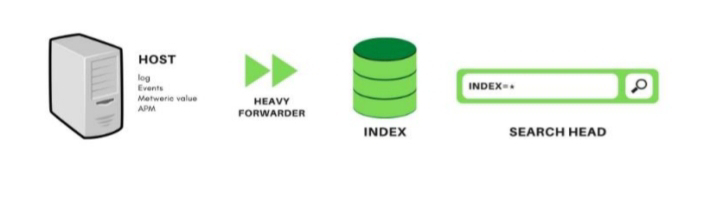
7. Heavy Forwarders : In some cases, heavy forwarders are used to preprocess data before sending it to the indexers. They can perform tasks like data parsing, filtering, and routing.
8. Universal Forwarders : These are lightweight forwarders designed for simple data collection and forwarding tasks.
Overall, Splunk's architecture is scalable, allowing organizations to deploy it in various configurations to meet their specific needs for data collection, indexing, searching, and visualization..
• Splunk Installation..
• Download splunk visit the splunk website (https://www.Splunk.Com/)
and navigate to the downloads section.
• Choose the appropriate version of splunk for your operating system
and download the installer package.
• Once the installer package is downloaded, locate the file and run it to
start the installation process.
• After installation, splunk will prompt you to configure the instance.
You will need to set up an administrator username and password, as
well as other configuration settings such as the data inputs and
indexes. Splunk is running on (http://localhost:8000) localhost use
port 8000.
• Splunk Components..👇🏻
2. Indexers: Indexers receive data from forwarders, index it, and store it in searchable indexes. They handle search requests and provide data querying capabilities.
3. Search Heads : Search heads provide the user interface for interacting with Splunk. They accept search requests from users, send them to indexers for processing, and display the results..
• Splunk Component - Forwarder
consume and send data to the
index.
•. It require minimal resources and have little impact on performance.
•. It is the primary way data is supplied for indexing.
• Splunk Component - Indexer.
• Indexer processes machine data, storing the results in indexes as events, enabling fast search and analysis.
• As the indexer indexes data, it creates a number of files organized in
sets of directories by age.
• Splunk Component – Search Head
• Allows users to use the search language to search the indexed data.
• Distributes user search requests to the indexers.
• Consolidates the result and extracts field value pairs from the events
to the user...
• Basic queries 👇🏻
Splunk Queries
1. Query to specify the index to search
Index=web_logs
2. Query to initiates a search for events based on specified criteria
Index=web_logs status=200
3. Query to filters events based on the specified sourcetype
sourcetype=apache_access
4. Query to filter events based on conditions
Index=logs | where status = “error”
5. Query to identify failed login attempts:
sourcetype=auth* "authentication failure”
| Stats count by user
| Sort –count
4. Query to identify potential security threats:
sourcetype=access_* method=post status=200 |
Rex field=_raw "password=(?[^&]+)"
| Eval password_length=length(password)
| where password_length >= 8
6. Query to identify privilege escalation attempts:
sourcetype=linux_secure su*
| where user!=Root AND user!="
7. Query to identify failed SSH attempts:
sourcetype=linux_secure "failed password for"
| stats count by src_ip
| Sort -count
8. Query to identify successful SSH attempts:
sourcetype=linux_secure "accepted publickey for”
| Stats count by src_ip
| sort -count
9. Query to identify network port scans:
sourcetype=network_traffic
| Stats count by src_ip, dest_port
| where count > 100
• For more click Here👇🏻



Comments
Post a Comment